Za studente i ostale zainteresirane, neke ideje za seminarske radove, diplomske...
Forenzička analiza društvenih mreža Prikazati društvene mreže
(facebook, linkedin i sl.) načine upotrebe, te načine rada tih sustava. Za
takve sustave objasniti što mogu biti artefakti i dokazi, te koje se metode i
načini mogu primjeniti za pronalaženje, akvizijciju i analizu tih dokaza i artefakaka.
Forenzička analiza mobilnih uređaja baziranih na Android operacijskom
sustavu Proučiti i istražiti forenzičku
analizu mobilnih uređaja koji koriste Android operacijski sustav. U radu se
treba osloniti na korištenje dostupnih nekomercijalnih alata i komercijalnih
alata u smislu kontrole. Ustanoviti pouzdanost forenzičke akvizicije podataka
iz mobilnog uređaja i opisati cijeli postupak na praktičnom primjeru
Postupak akvizicije digitalnog medija Prikaz i analiza postupaka
akvizicije digitalnog medija u računalnoj forenzici
Simulatori računalnih mreža i sustava Pregled i analiza simulatora
računalnih mreža i sustava
Računalni forenzički jezik visokog nivoa Izrada specifikacije za računalni
forenzički jezik visokog nivoa, na osnovi postojećih alata u phytonu i drugim
jezicima
Primjena računalne forenzike na inteligetnim kućnim uređajima Prikazati metode računalne
forenzike na inteligetnimkučnim uređajima tj uređajima koji sadrže računalne i
druge eletroničke komponene a koriste se u kučanstvu
Alati računalne forenzike u jeziku python Istražiti mogučnosti alata za
računalnu forenziku baziranih na jeziku python. Posebno razraditi repozitorije
alata, pronalaženje alata prikladnog za neki problem, te korištenje alata na
odabranoj platformi i moguću integraciju ili povezivanje sa drugim forenzičkim
alatima
Implementacija prospojnika drugog sloja u otovorenom kodu Proučiti i razraditi mogučnosti
implementacije prospojnika drugog sloja u otovorenom kodu (open source layer 2
switch) u računalnim mrežama
Forenzika račualnih i mrežnih sustava u modernim automobilima Prikazati računalne i mrežne
sustave u modernim automobilima. Na osnovi analize dostupnih podataka o radu
tih sustava predložiti i razraditi metodologiju i postupke forenzike takvih
računalnih sustava.
Računalna forenzika i vritualizacija sustava Korištenje virtualizacije u
postupicma računalne forenzike, te forenzika virtualiziranih sustava
Forenzika aktivne mrežne opreme Forenzički postupci za aktivnu
mrežnu opremu.
Forenzika baza podataka Računalna forenzika sustava baza
podataka i sustava za trajnu pohranu podataka
Kučanski roboti i računalna forenzika Potrebno je razraditi forenzičku
analizu kučanskih robota poput robota usisivača, robota čistaća i drugih slični
uređaja.
Industrijski roboti i računalna forenzika Potrebno je prikazati i razraditi
metode računalne forenzike za robotizirane industrijske sustave.
Dgitalni sustavi video nadzora i metode računalne forenzike Potrebno je prikazati primjenu
računalne forenzike na sustavim digitalnog video nadzora.
Održavanje kontinuiteta poslovanja IT sustava Prikazati metode održavanja
kontinuiteta poslovanja za IT sustav. Razraditi metode prkupljnja i analize
podataka bez namjenskih programskih alata.
Održavanje kontinuiteta poslovanja Teoretksi obraditi sustav za
nastavak poslovanja, pri tome se služiti postojeći standardima i praksom sa
podrucja kontinuiteta poslovanja. Kao praktični dio razviti web bazirani sustav
za kontrolu i provođenje kontinuiteta poslovanja.
Cyberwarfare napadački programi Prikaz rada i ofenzivnog ponašanja
ratnog koda. Potrebno je prikazati kako radi prvi pravi ratni napadacki program
stuxnet crv te naične obrane i detekcije tog crva.
Sustavi za automatsko trgovanje Opisati i analizirati sustave za
automatsko trgovanje na burzama. Posebno proučiti probleme sigurnosti takvih
sustava i na izvedbenoj i na algoritamskoj osnovi
Pregled modela digitalne forenzike Navesti, prikazati i objasniti
modele izvođenja digitalne forenzike. Predložiti moguća rješenja za probleme
zaostatka u forenzičkim laboratorijama te predložiti metodološke i tehničke
mjere koje se mogu primjeniti za smanjenje zaostataka. Ocjeniti moguće
modifikacije potojećih alata i procedura u skladu sa predloženim mjerama i
modelima
Krizno umrežavanje Prikazati izgradnju jednostavne
wifi mreže bazirane na ofshelf kompomentama i opensource kodu koja bi omogučila
funkcioniranje i u slučaju ispada glavni IP i GMS providera.
Sigurno brisanje medija za pohranu podataka Prikazati i razraditi tehnike
sigurnog brisanja podataka sa medija za pohranu. Posebno razraditi slučajeve
novih tehnologija kao što je SSD
Korištenje Android simulatora u digitalnoj forenzici Proučiti mogučnosti simulatora ili
korištenja virtualnog Android operacijskog sustava u forenzičkim postupcima.
Pri analizi mobinih i drugih uređaja pod Andriod operacijskoim sustavom
potrebno je ustanovit stanja uređaja, ponovo ga pokrenuti da se vidi ponašanje
aplikacija i sl, a za te primjene isprobati simulator ili virtualni andorid te
proučiti načine prenošenja slike uređaja u takvo simulirano okruženje.
Predložiti postupke i navesti prednosti i nedostatke.
Mogučnosti primjene CFengine sustava u računalnoj forenzici Potrebno je proučiti mogučnosti
primjene upravljačkog i sigurnosnog sustava CFengine u okvirima live
forenzičkih zadataka mrežnih računalnih sustava.
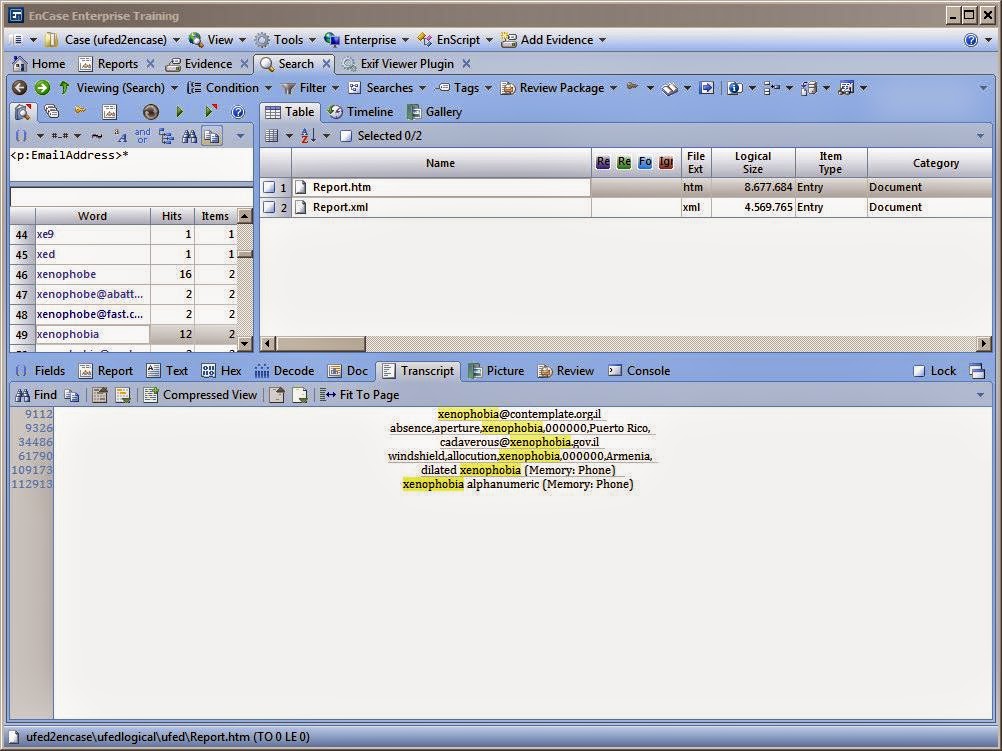
Forenzička analiza metadata podataka u postojećim formatima dokumenata Analizirati poznate formate dokumenata
za digitalne slike, digitalne dokumente, elektroničku poštu i druge tipove
digitalnih dokumenata. Na osnovi forenzičke analize razraditi mehanizme
izdvajanja metapodataka iz dokumenata i u mirovanju i mrežnom prijenosu i na
osnovu tih mehanizama prikazati sigurnosne rizike te mehanizme uklanjanja tih
rizika. Korištenjem dostupnih alata demonstrirati rezultate analize i otkrivene
rizike